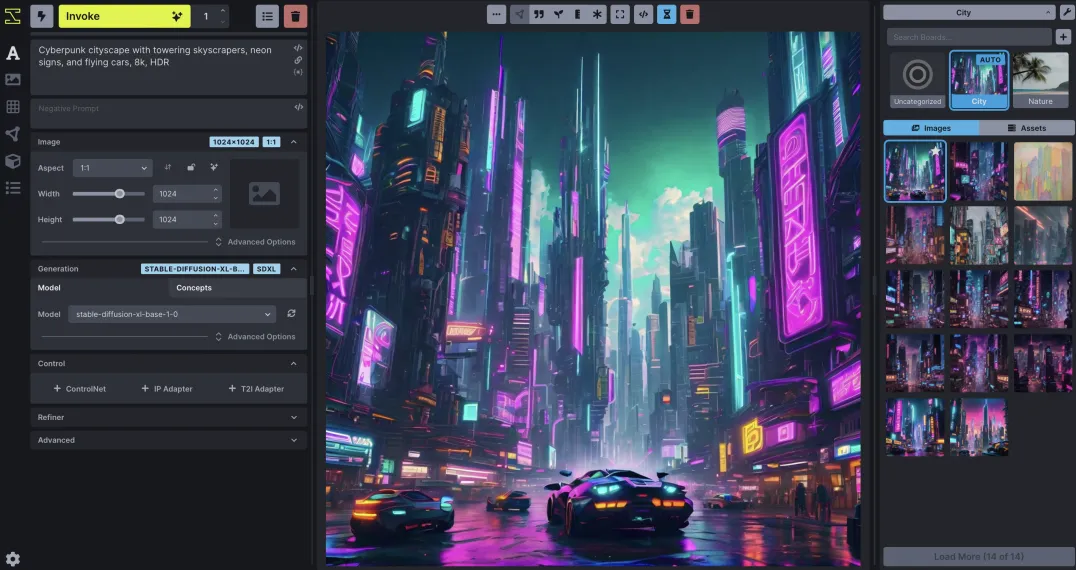
Russian hackers exploit Microsoft Hyper-V to hide Linux-based malware and evade detection
A group of Russian hackers, known as Curly COMrades, was discovered using an unusual tactic to hide malware inside Linux virtual machines by abusing Microsoft’s Hyper-V technology. This method allows attackers to run malicious tools in an isolated environment, thereby evading traditional Endpoint Detection and Response (EDR) systems and maintaining persistent access to victims’ networks.
The Role of Agentic AI in Cyber: Future Trends Overview
As technology continues to advance at an unprecedented pace, the role of artificial intelligence (AI), particularly agentic AI, is becoming increasingly significant in shaping the future of the cyber landscape. Agentic AI refers to systems that possess a degree of autonomy, allowing them to make decisions, learn from experiences, and act independently based on programming and data input. This article explores the implications of agentic AI on future cyber trends.
Latest Trends in Cybersecurity and AI
The integration of artificial intelligence (AI) into cybersecurity has accelerated, shaping the landscape of digital security. As cyber threats continue to evolve, organizations are adopting new strategies and technologies to counter these challenges. Below are the latest trends in the intersection of cybersecurity and AI:
Critical Next.js Security Vulnerability Enables Middleware Authorization Bypass
A critical vulnerability has been identified in the Next.js React framework, posing a significant security risk by allowing attackers to bypass middleware-based authorization checks under specific circumstances.
The flaw, identified as CVE-2025-29927, has received a CVSS severity rating of 9.1 out of 10, underscoring its critical nature.
Vulnerability CVE-2022-40648 exploited by Belsen Group
In 2025, the cyber security landscape was shaken by the official debut of the Belsen Group – a new group that exploited over 15,000 vulnerable configurations of FortiNet firewalls in 144 countries. This event not only highlights the risks associated with known vulnerabilities but also serves as a lesson about the importance of compromise assessments and prompt remediation.
The Belsen Group entered the cyber scene with a post on the dark web stating:
5 Open-source Local AI Tools for Image Generation that work best
I discovered these interesting open-source Local AI Tools for image generation that run locally. Explore their features, capabilities, and how they empower creativity without relying on cloud services.
Ever since I realized that AI was shaping the future, I’ve been fascinated by its endless possibilities.
I’m someone who enjoys testing large language models (LLMs) on my devices, and the open-source approach to data has always been my preference.
The Evolution of Cybersecurity Governance: Adapting to a New Era of Risk and Resilience
Cybersecurity governance has undergone a massive transformation over the past few decades. What once functioned as a peripheral concern, an afterthought to business operations, has now become a central pillar of enterprise risk management. Today, security is no longer just an IT function; it is a strategic imperative that demands board-level attention.
The 18 biggest data breaches of the 21st century
In today’s data-driven world, data breaches can affect hundreds of millions or even billions of people at a time. Digital transformation has increased the supply of data moving, and data breaches have scaled up with it as attackers exploit the data-dependencies of daily life. How large cyberattacks of the future might become remains speculation, but as this list of the biggest data breaches of the 21st Century indicates, they have already reached enormous magnitudes.
Top 10 Linux Distros in 2025
Linux is a free and open-source Unix-based operating system. As a result of Linux's security and flexibility, its use is gaining a great deal of attention these days. A Linux distro is an operating system that relies on the Linux kernel.
A Linux server or high-end cloud device might be used on a desktop computer or laptop, but on a personal computer or laptop, it can be difficult to use. However, times have changed since then.
RansomHub: Who is the cyber actor that has surpassed LockBit at the top of ransomware groups?
The RansomHub group has recently emerged in the ransomware scene, but that doesn’t mean it has failed to gain rapid notoriety for its sophisticated attacks. This article aims to analyze the group by exploring its history, operational methods, and compromised victims.