
The RansomHub group has recently emerged in the ransomware scene, but that doesn’t mean it has failed to gain rapid notoriety for its sophisticated attacks. This article aims to analyze the group by exploring its history, operational methods, and compromised victims.
Origins and Evolution
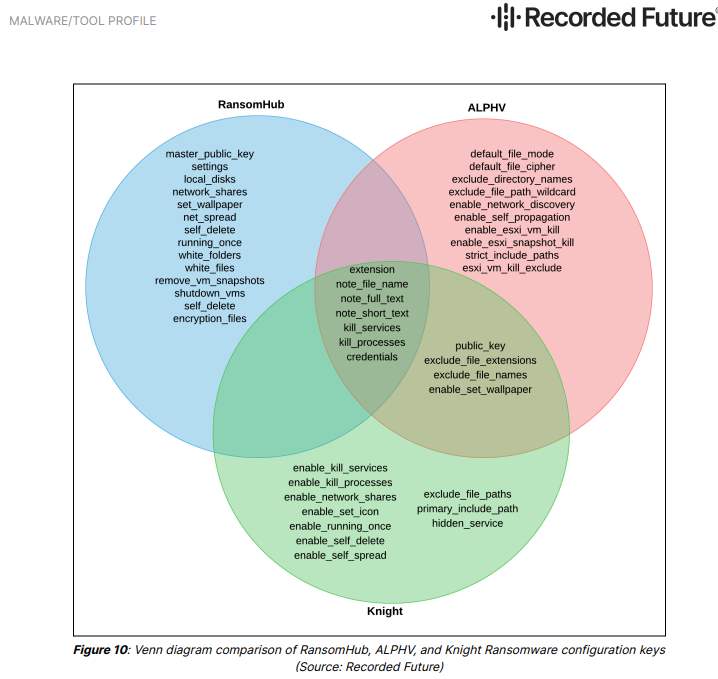
According to currently available data, the RansomHub group was established in early 2024, with potential links to previous ransomware groups ALPHV (also known as Noberus or BlackCat) and Knight (a rebranded version of the Cyclops group). This connection was established due to overlaps in the malware source code used by RansomHub and the two aforementioned groups.
The ALPHV group quickly made a name for itself in the industry by adopting a Ransomware-as-a-Service (RaaS) business model, offering access to its malware and infrastructure to other cybercriminals for a fee. These highly effective resources have been used to compromise high-profile companies. Currently, the U.S. Department of State has offered a reward of $15 million for information leading to the identification of ALPHV group members.
The U.S. Department of State is offering a reward of up to $10,000,000 for information leading to the identification or location of any individual(s) who hold a key leadership position in the Transnational Organized Crime group behind the ALPHV/BlackCat ransomware variant. In addition, a reward offer of up to $5,000,000 is offered for information leading to the arrest and/or conviction in any country of any individual conspiring to participate in or attempting to participate in ALPHV/BlackCat ransomware activities.
The Knight/Cyclops group – Its source code was put up for sale on a dark web forum in February 2024 after Knight's developers decided to shut down operations. It is possible that other actors purchased the commercialized source code to leverage it for launching new ransomware groups.
Why Is RansomHub Gaining Ground So Quickly?
A key factor behind RansomHub's rapid rise in notoriety is the fact that it offers affiliates a 90% commission rate, a considerably high percentage in the RaaS market. This lucrative rate is likely to attract experienced affiliates from other platforms, leading to an increase in infections and victims in the future. To instill confidence in potential collaborators, the RansomHub website features the following message:
Join our alliance advantage?
We only share 10%, and the alliance can take 90% of the payment.
With your wallet address for receipt, we do not limit the payment method. Pay you at first, then pay 10% to us.
Additionally, this ransomware stands out for its multi-OS approach, offering solutions targeting operating systems such as Windows, Linux, and ESXi, a critical feature that significantly broadens its range of potential victims.
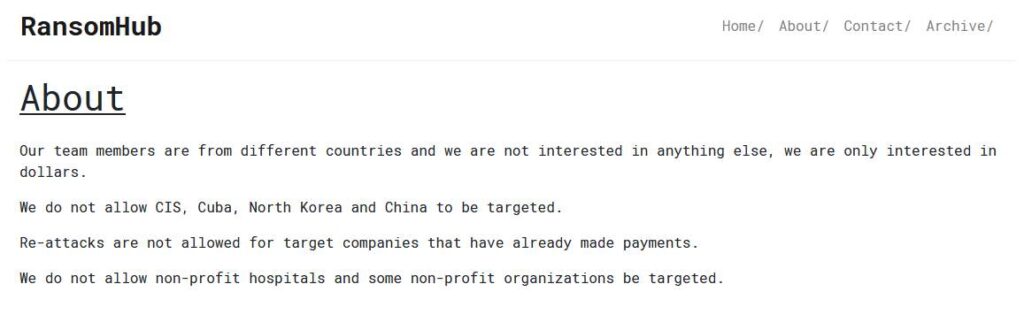
RansomHub operators publicly state that their motivation is purely financial. They do not target entities from the Commonwealth of Independent States (CIS), Cuba, North Korea, or China, and attacks on hospitals, non-profit organizations, and companies that have already paid the ransom are also prohibited.
RansomHub’s Attack Methods
RansomHub employs a variety of techniques to compromise its victims, including phishing tactics, exploiting software vulnerabilities, and brute-force attacks. Once access is gained, attackers install the RansomHub malware, encrypt the victim's files, and demand a ransom for decryption.
RansomHub’s Victims
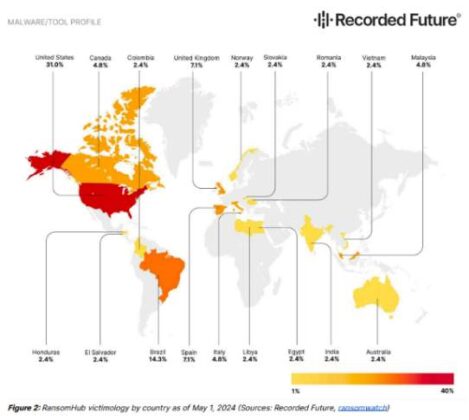
Between February 2024 and the present, the group has compromised 92 entities, including two companies with operations in Romania – NTT DATA and Farmacia AL-SHEFA. Such a figure—92 victims in just five months—represents an alarming trend.
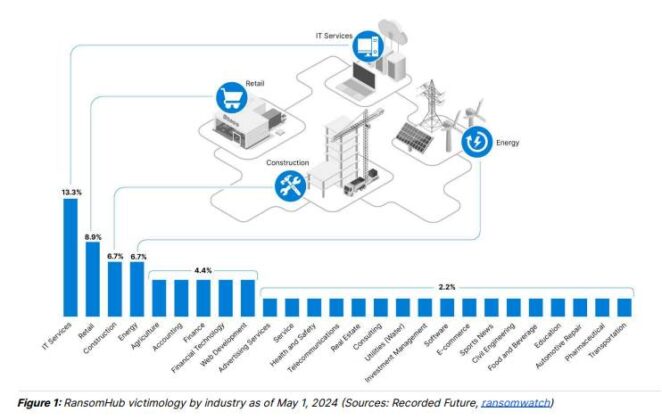
RansomHub has become a significant cyber threat, posing a serious risk to organizations across multiple industries.

Add new comment